SOC Automation Project - Part 6 (Final)
Building a SOC automation Home Lab: Part 6 - Shuffle Integration
A step-by-step guide for building your very own SOC Automation Home Lab using VMWare and DigitalOcean cloud provider
In this final module of our series, we dive into leveraging Shuffle’s SOAR capabilities to automate crucial tasks within our Security Operations Center (SOC). Our focus will be on integrating Wazuh with Shuffle to streamline alert handling, utilizing VirusTotal for threat intelligence, and integrating with theHive for efficient case management.
Shuffle
Shuffle is an Open Source interpretation of SOAR. It aims to bring all the capabilities necessary to transfer data throughout an enterprise with plug-and-play Apps, making automation approachable for everyone.
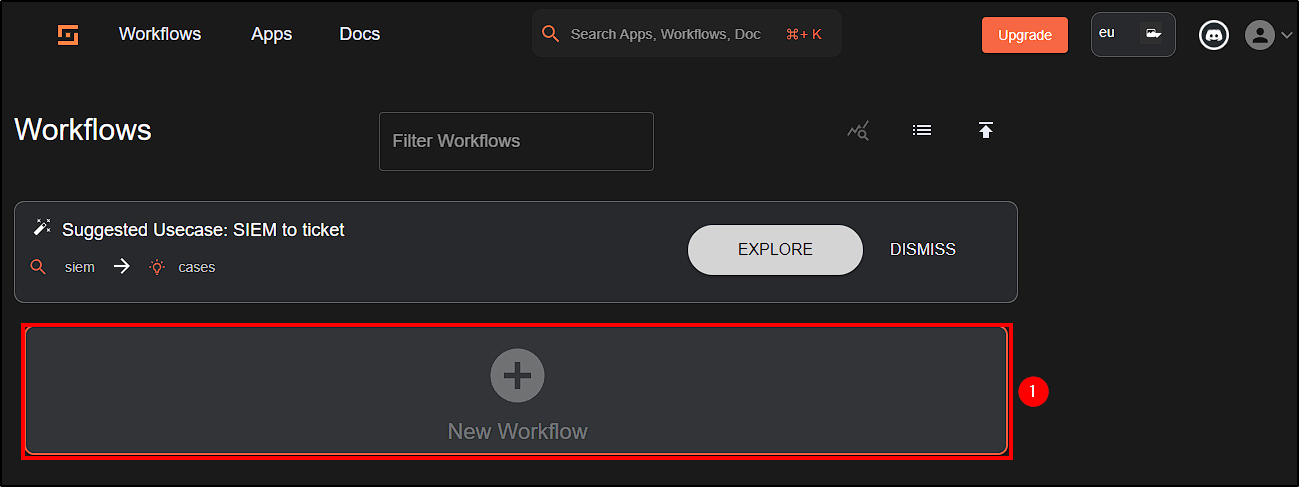
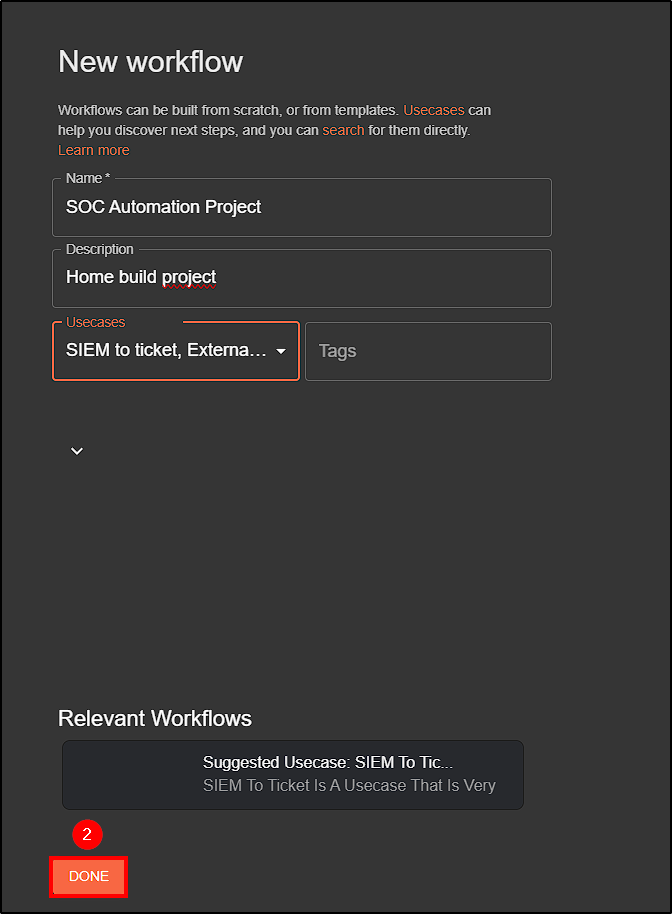
To get started, visit Shuffle and create an account. Once logged in, create a Workflow and name it.
In our workflow interface we will be able to add apps, triggers and variables that will enable us to automate some tasks.
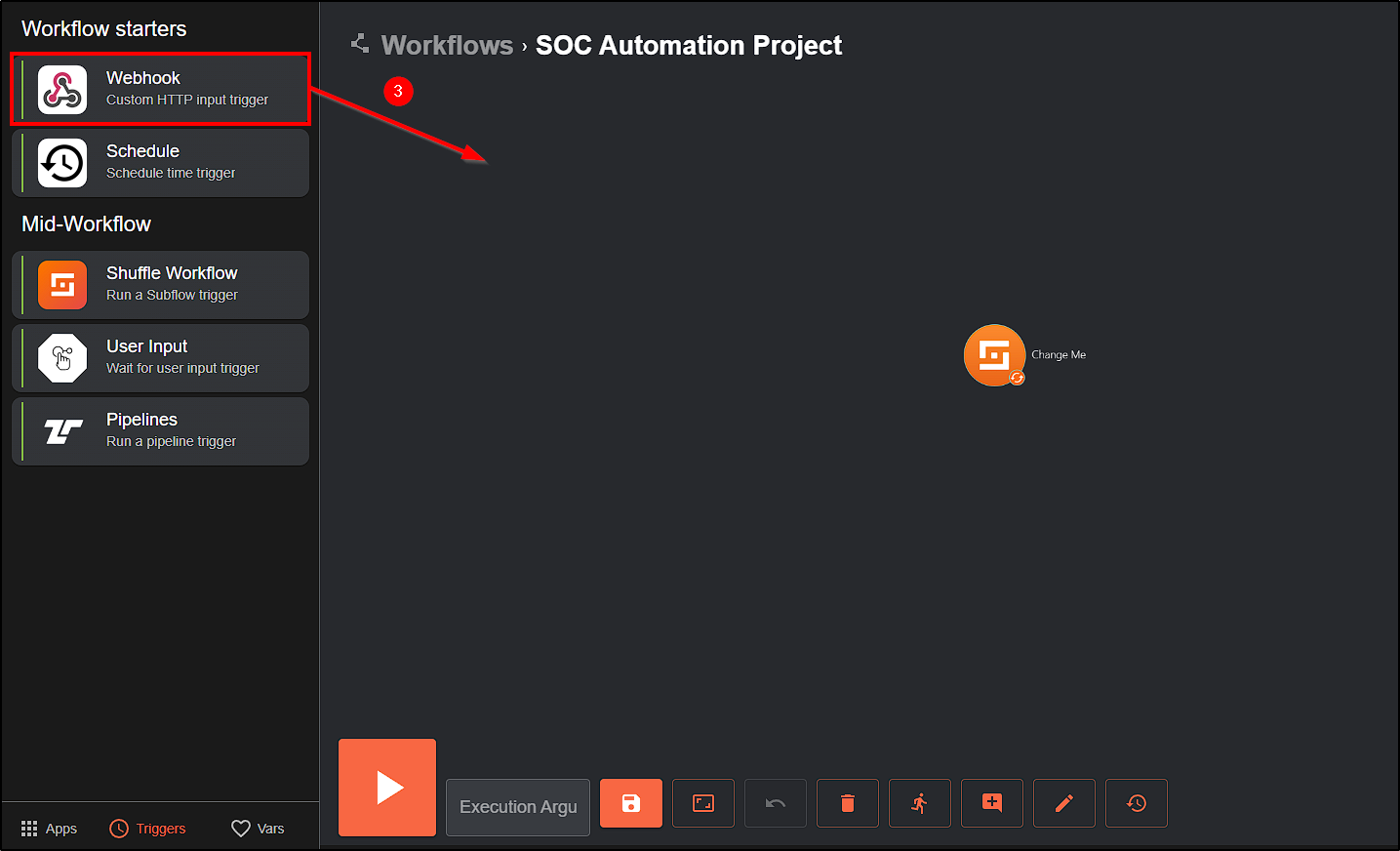
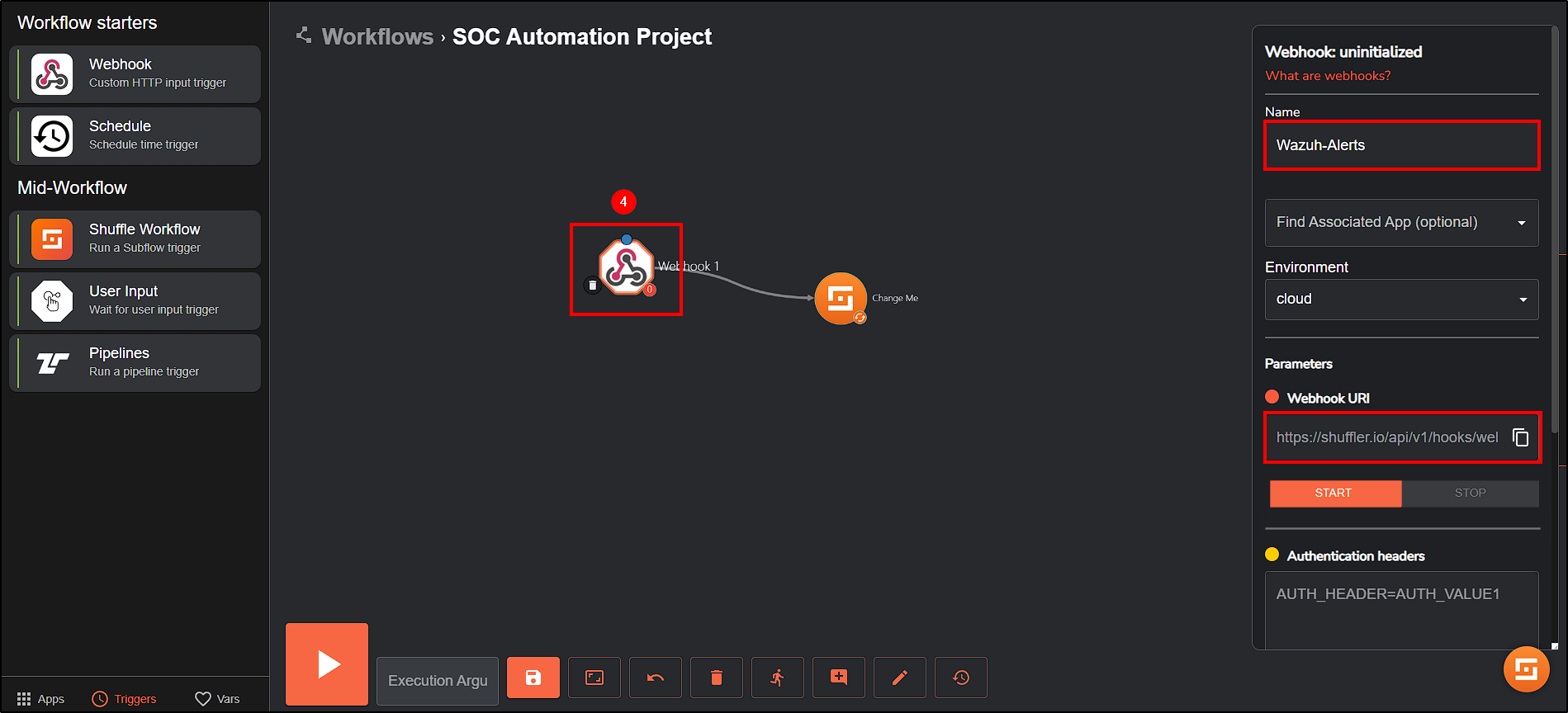
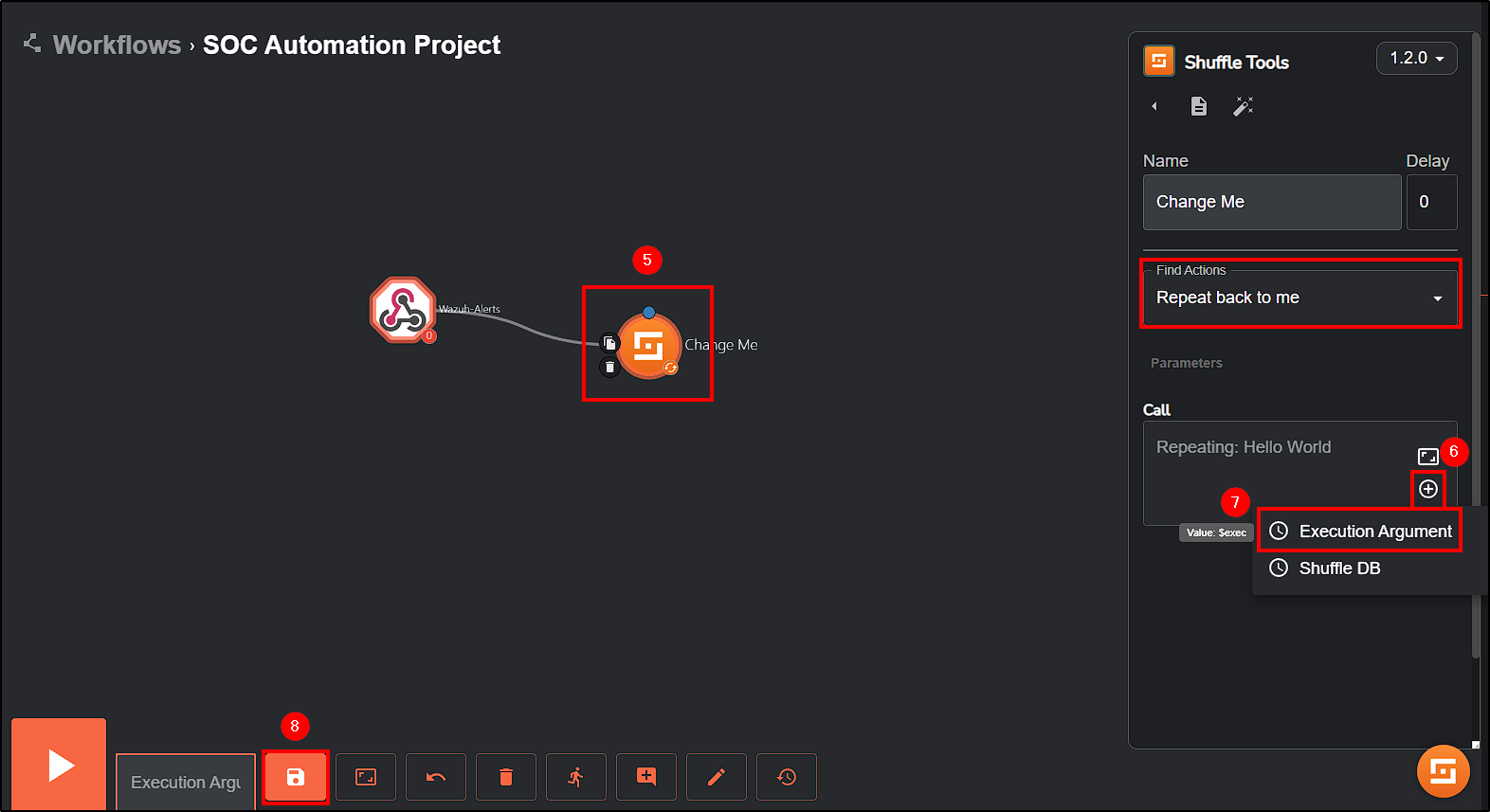
First, drag a Webhook to our workflow and connect it to the Change Me button. The Webhook function is to receive the alerts from Wazuh into our workflow in Shuffle.
Next, make the following changes in the Change Me button:
- Find Actions: leave it as
Repeat back to me. - Call: Remove “Hello World” and select
+ Execution Argument
This way, any alert received from our Webhook will repeat its content.
Save the changes and head back to Wazuh server SSH session to configure Wazuh.
Getting Wazuh Alerts to Shuffle
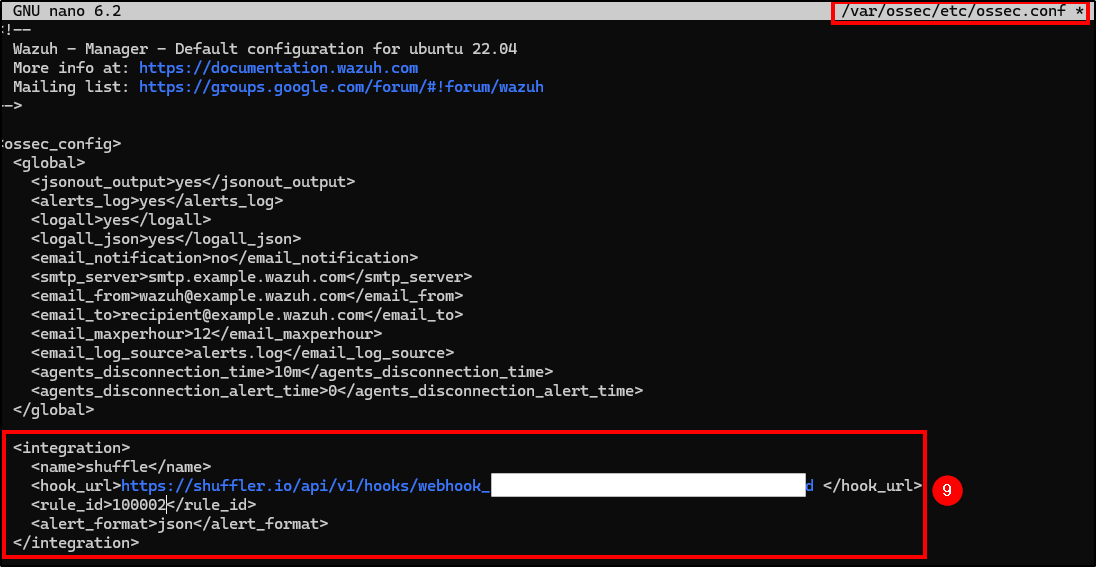
In order to connect Wazuh with Shuffle we need to add an integration tag in the ossec.conf file.
Open ossec.conf and add the following content:
1
2
# Configuring Wazuh
nano /var/ossec/etc/ossec.conf
Make sure the indentation is correct and separate the Webhook_URI from the closing hook_url tag!
1
2
3
4
5
6
<integration>
<name>shuffle</name>
<hook_url>"WEBHOOK_URI" <hook_url>
<rule_id>100002</rule_id>
<alert_format>json</alert_format>
</integration>
This configuration directs alerts related to rule ID 100002 (Mimikatz Detected) to Shuffle.
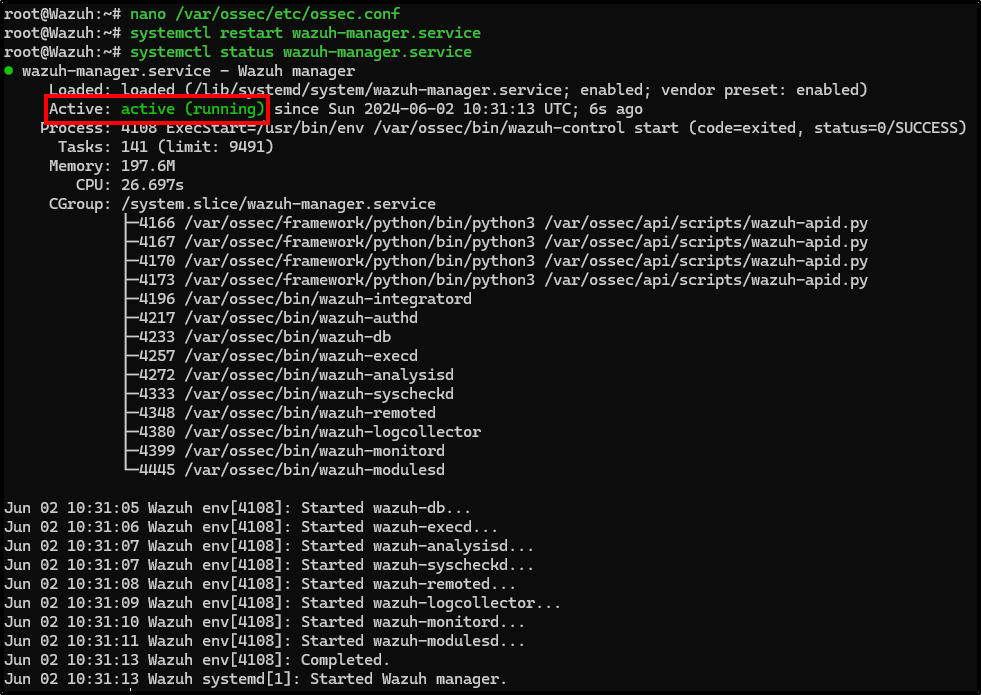
Save the file and restart the Wazuh manager service.
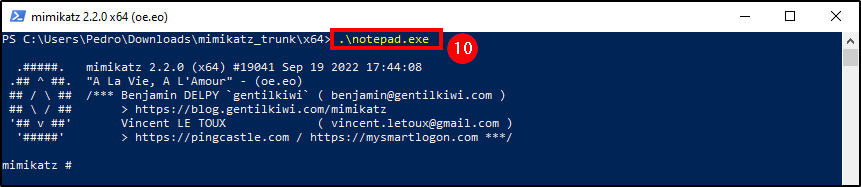
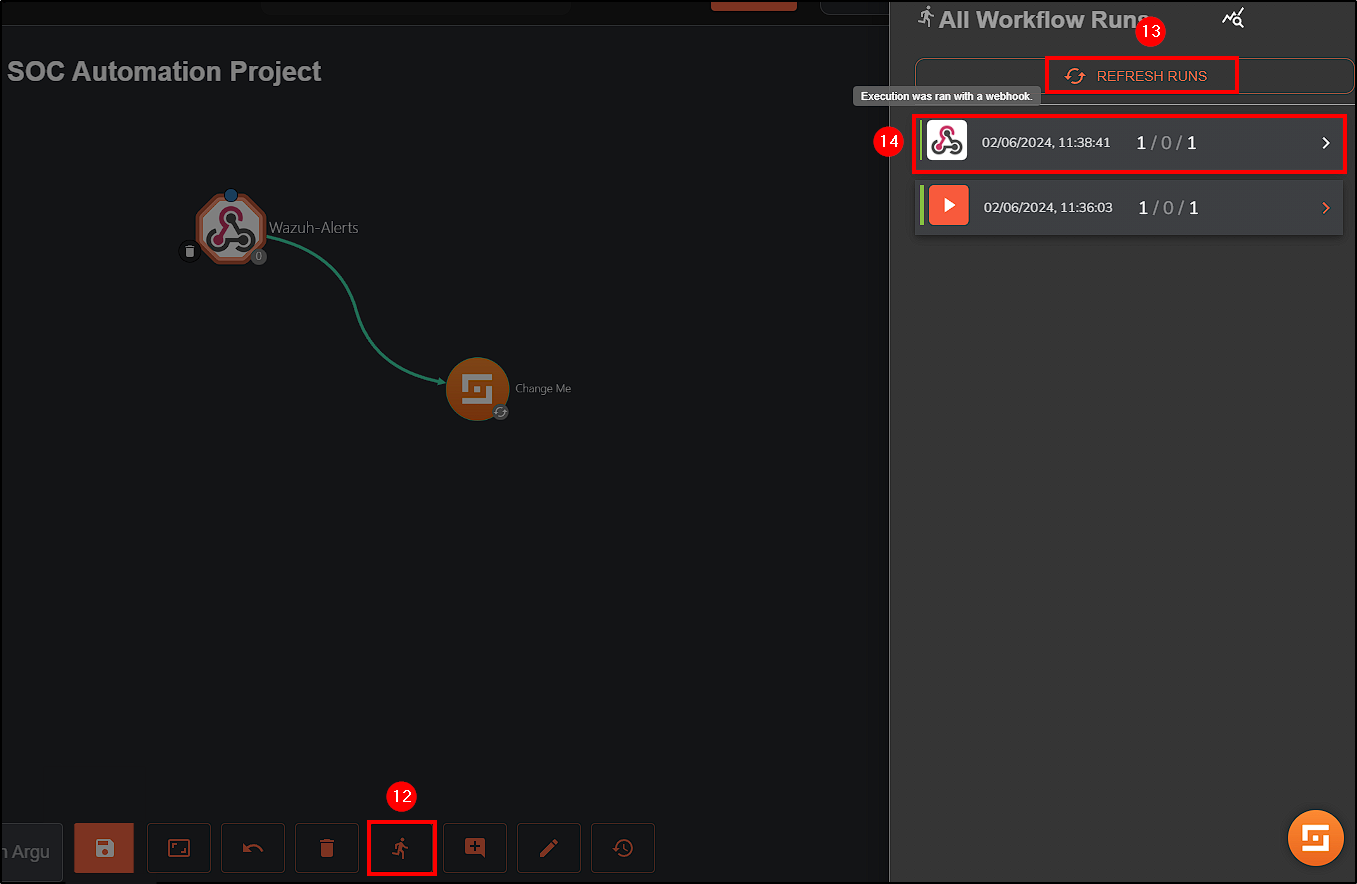
Before returning to Shuffle, rerun notepad.exe (mimikatz) on the Wazuh Agent to create an alert.
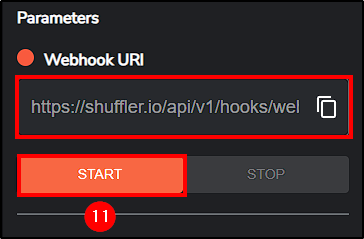
In Shuffle, click on the Webhook and select START.
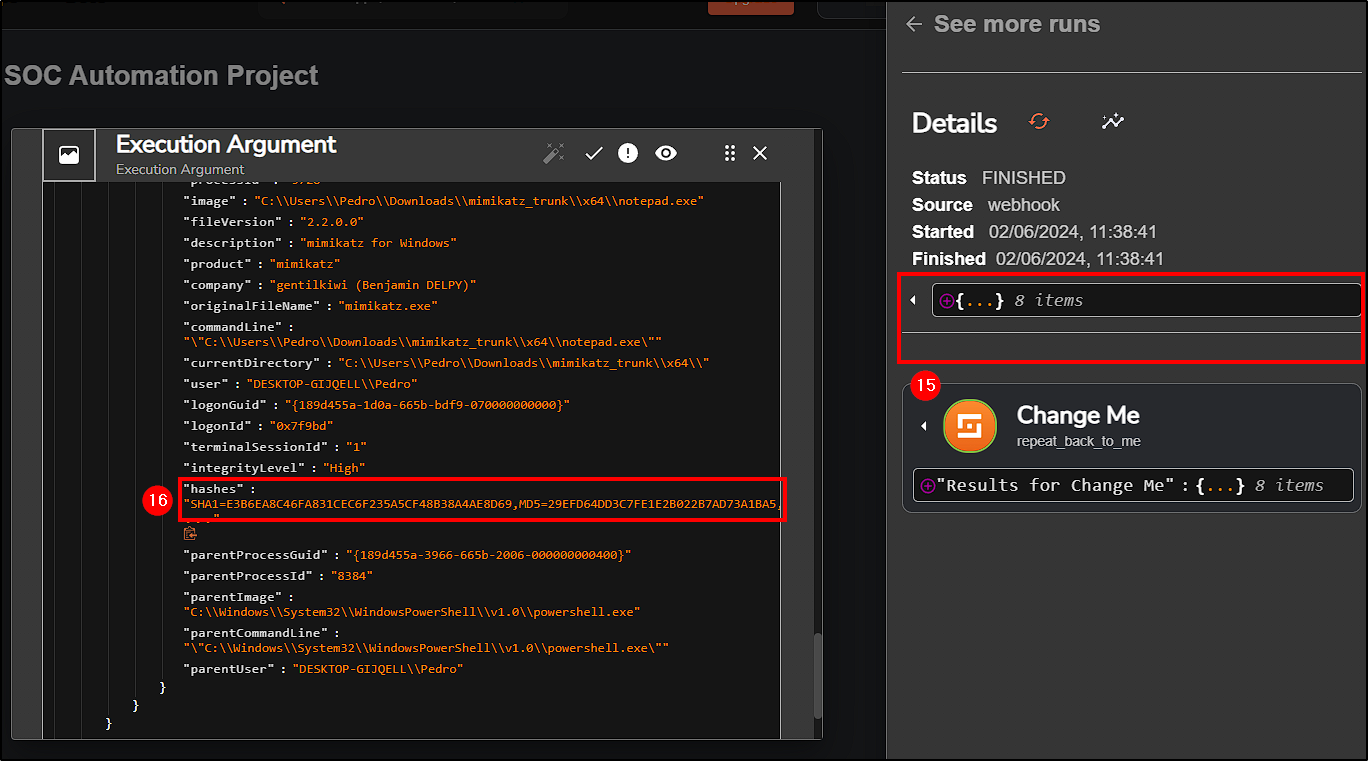
Next, select Show Executions and there should be some events from Wazuh. When inspecting Execution Argument’s content we can see that the alert is related to mimikatz.
IOC Enrichment
Now that Shuffle is receiving alerts from Wazuh, we can enrich the Indicators of Compromise (IOCs) from these alerts using apps like VirusTotal and AbuseIPdb.
In this case, let’s check mimikatz reputation with VirusTotal by checking its SHA256 file hash.
According to VT documentation, the format to obtain a file report is “/api/v3/files/{id}”.
For details on how to retrieve a file report from VirusTotal using their API, refer to the VirusTotal API v3 documentation
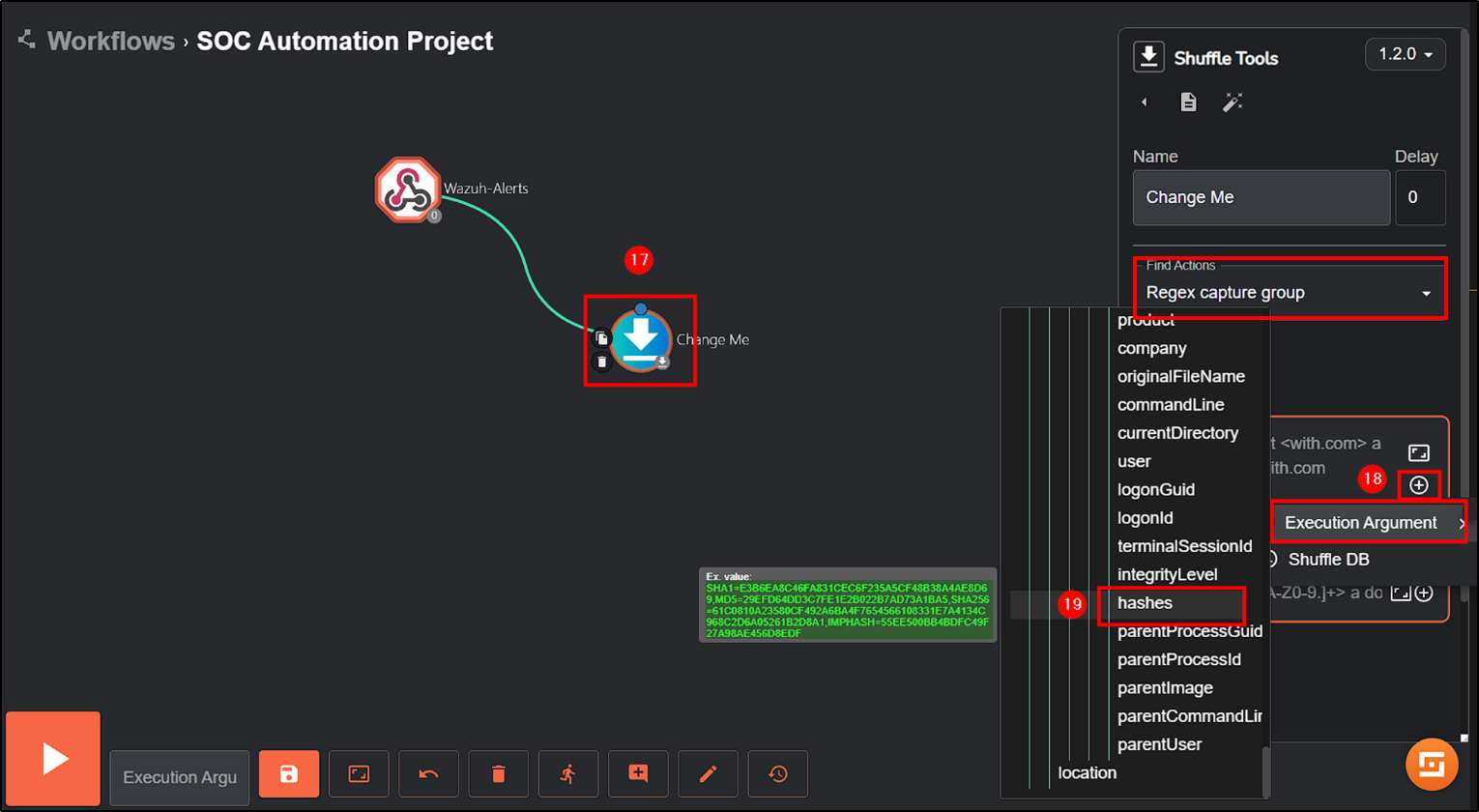
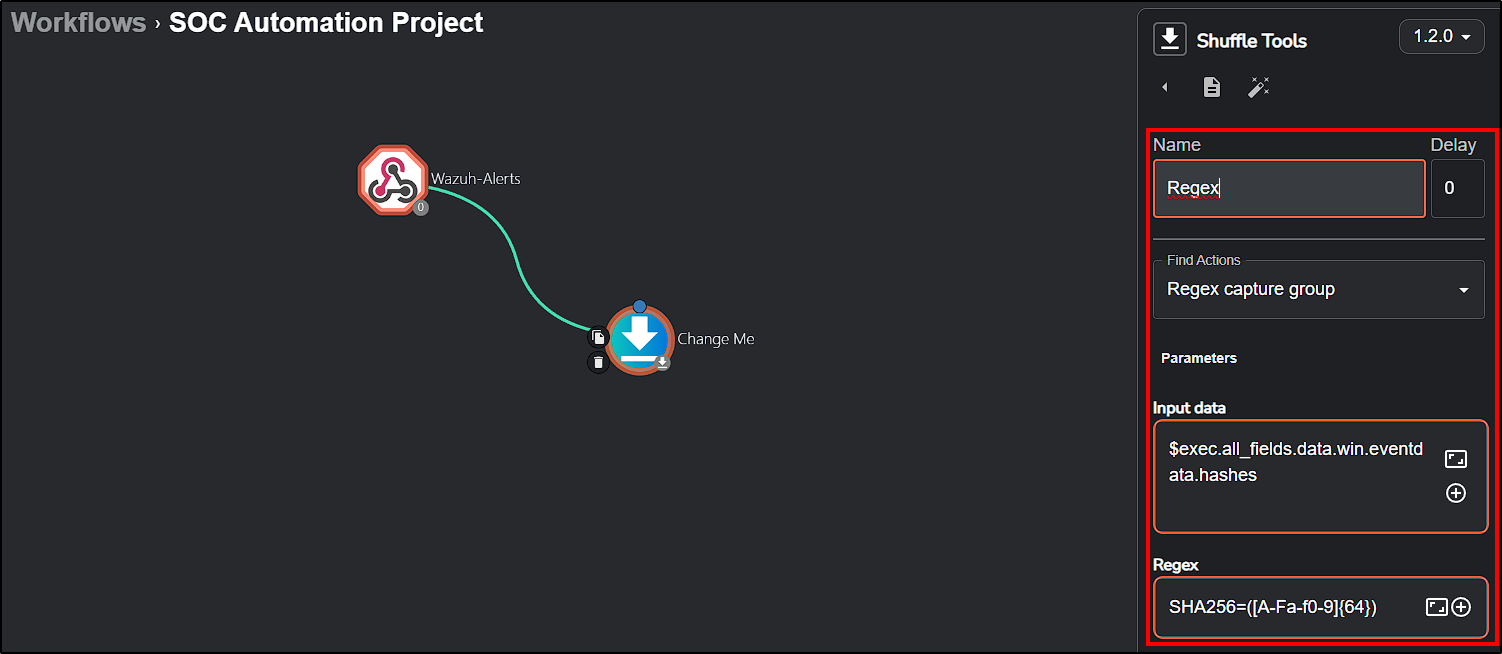
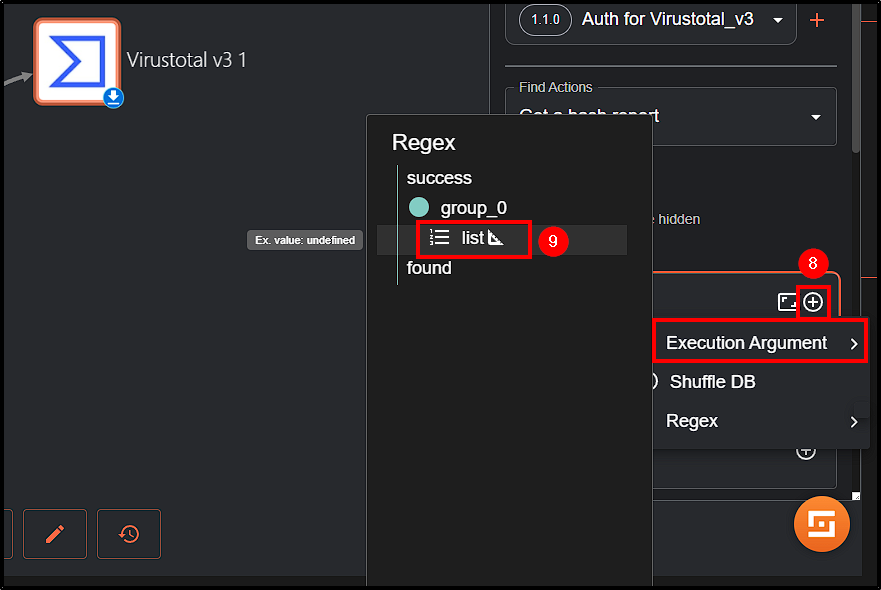
Since our alert contains multiple hashes (SHA1, MD5, SHA256, IMPHASH), our initial step is to extract the SHA256 hash value using Regex. We’ll modify the Change Me button accordingly:
- Find Actions: Change it to
Regex capture group. - Input data: Select the hashes value from Execution Arguments (
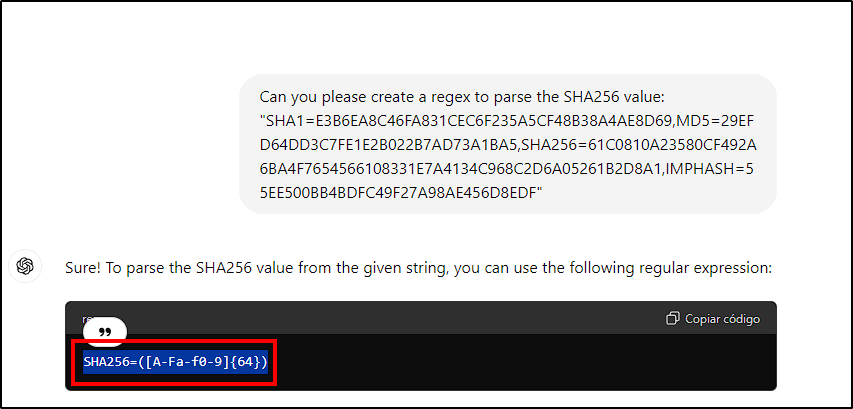
$exec.text.win.eventdata.hashes). - Regex: To only get SHA256 value use
SHA256=([A-Fa-f0-9]{64})(we can use ChatGPT to help you with it).
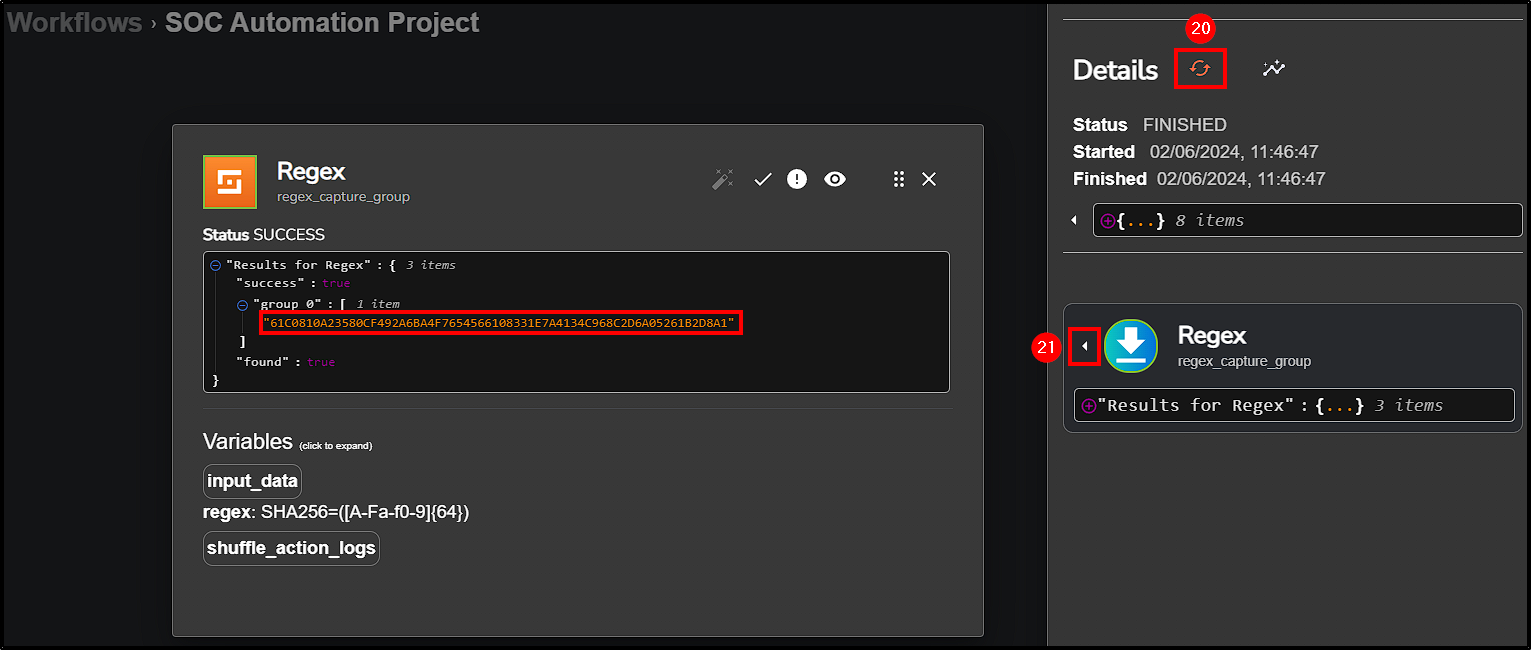
Next, test it to see if only the SHA256 hash value is received by selecting Rerun Workflow.
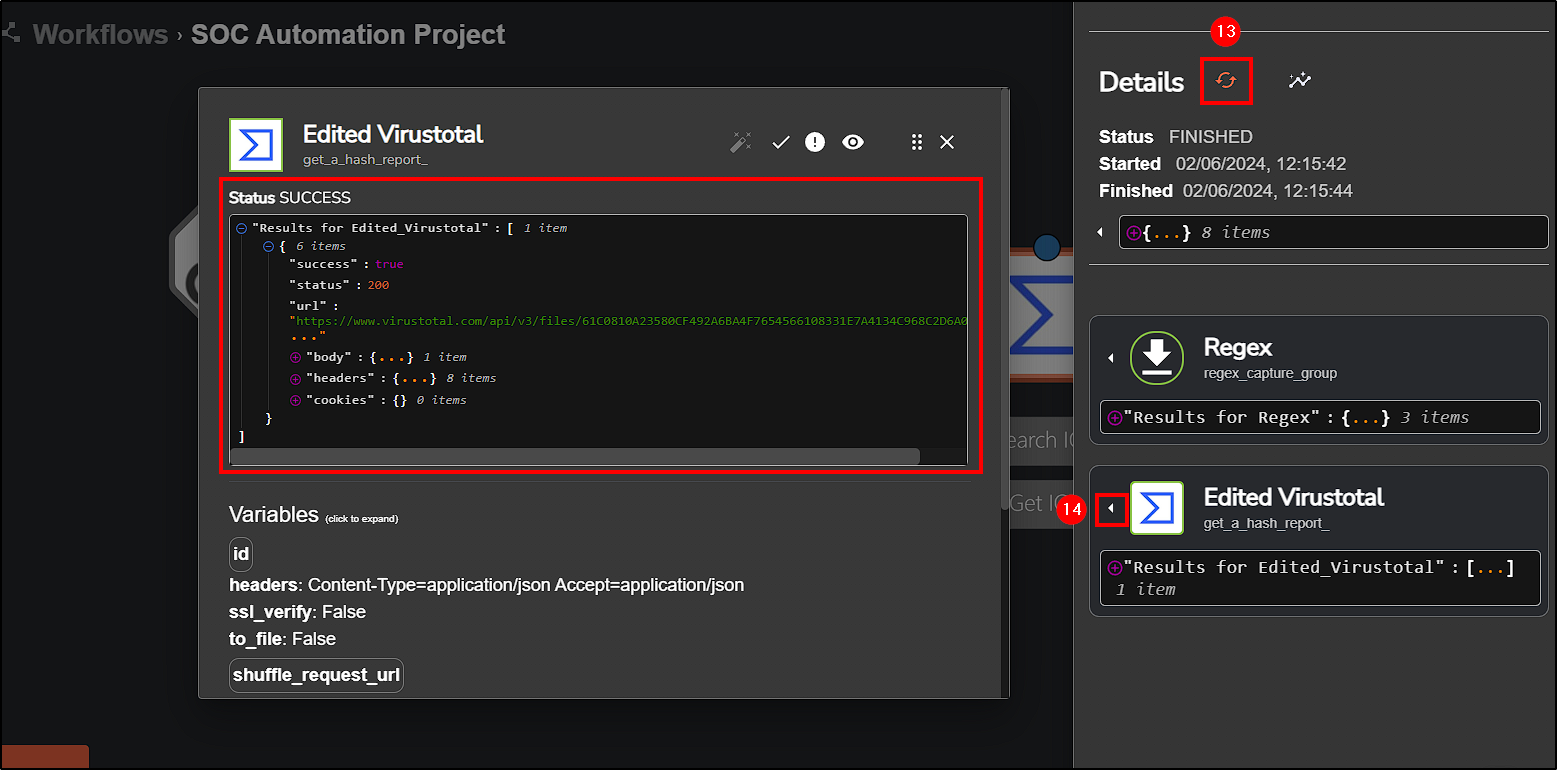
Now that we have our hash, our next step is to integrate VirusTotal in the workflow and get file reports from it.
VirusTotal Integration
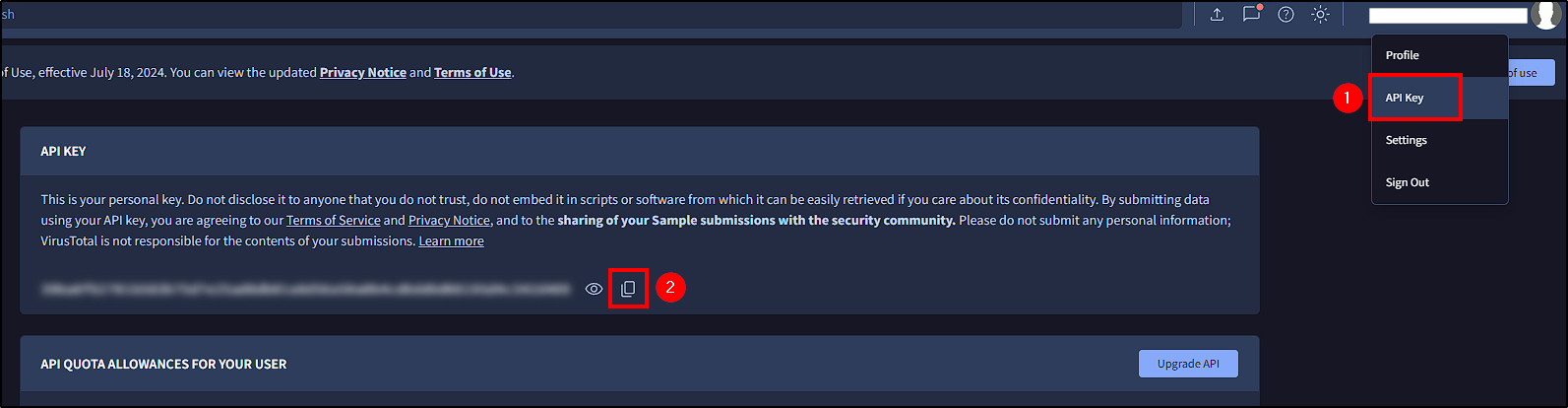
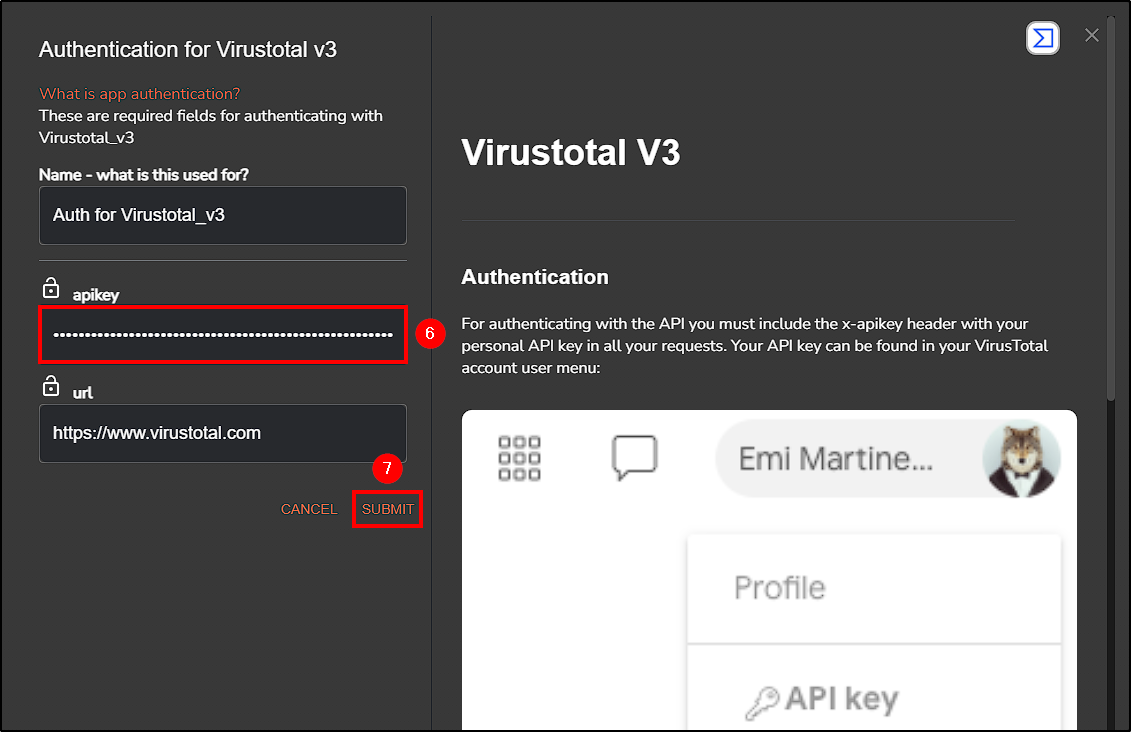
First, authenticate to VirusTotal and copy its API key that will allow us to authenticate on Shuffle.
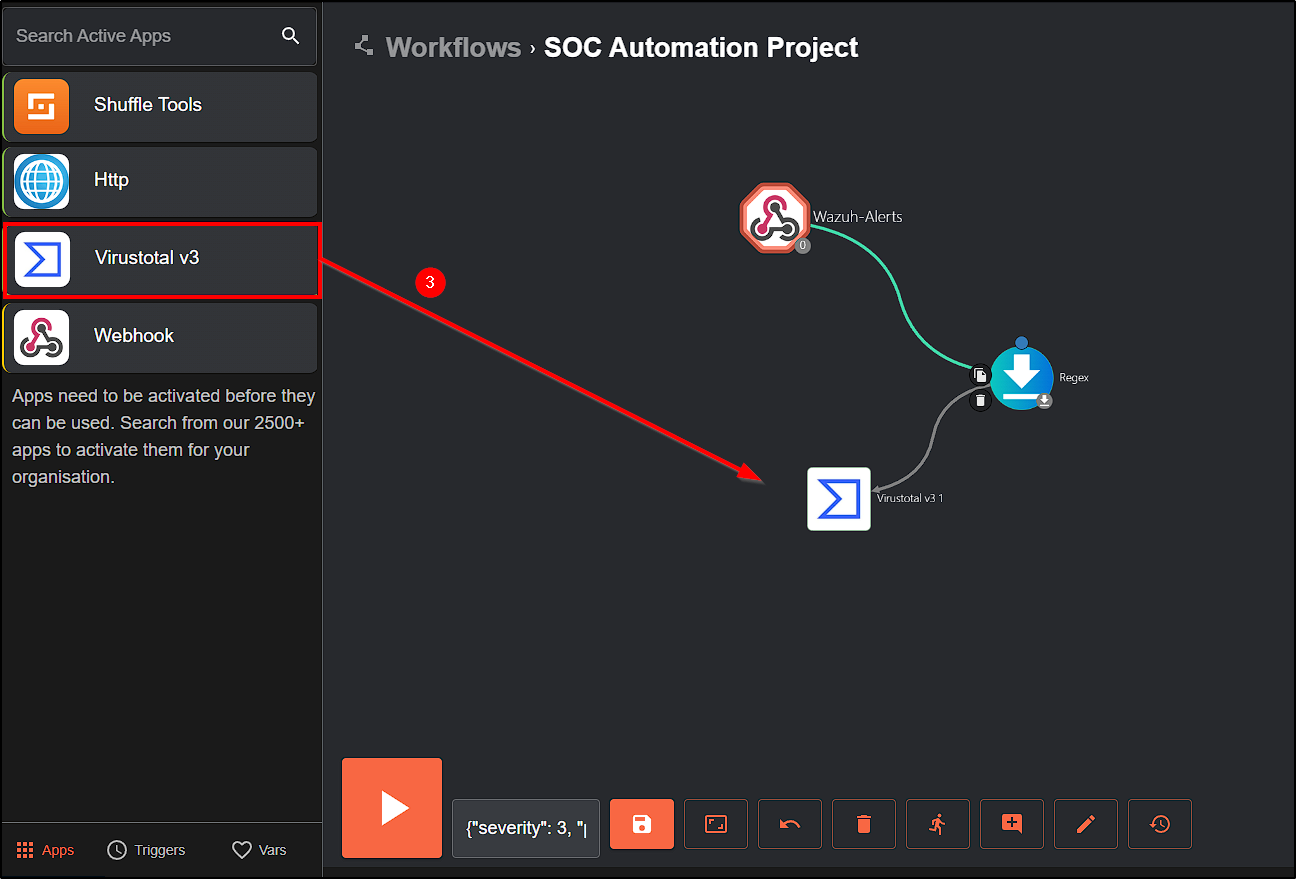
Head back to Shuffle, drag the VirusTotal app to our workflow and complete the authentication process.
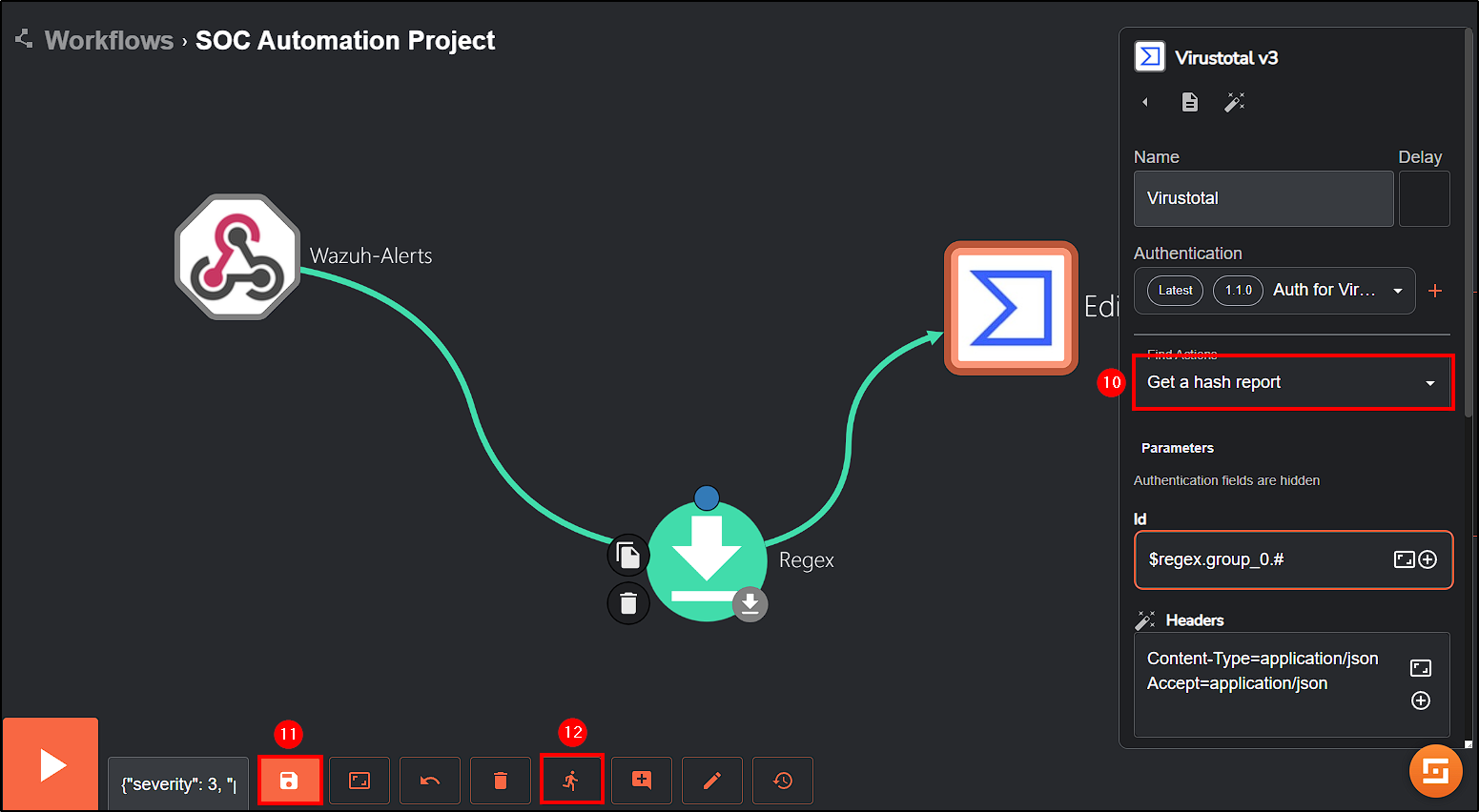
Next, change the Find Action parameter to Get a hash report and the Id to the regex value we set before.
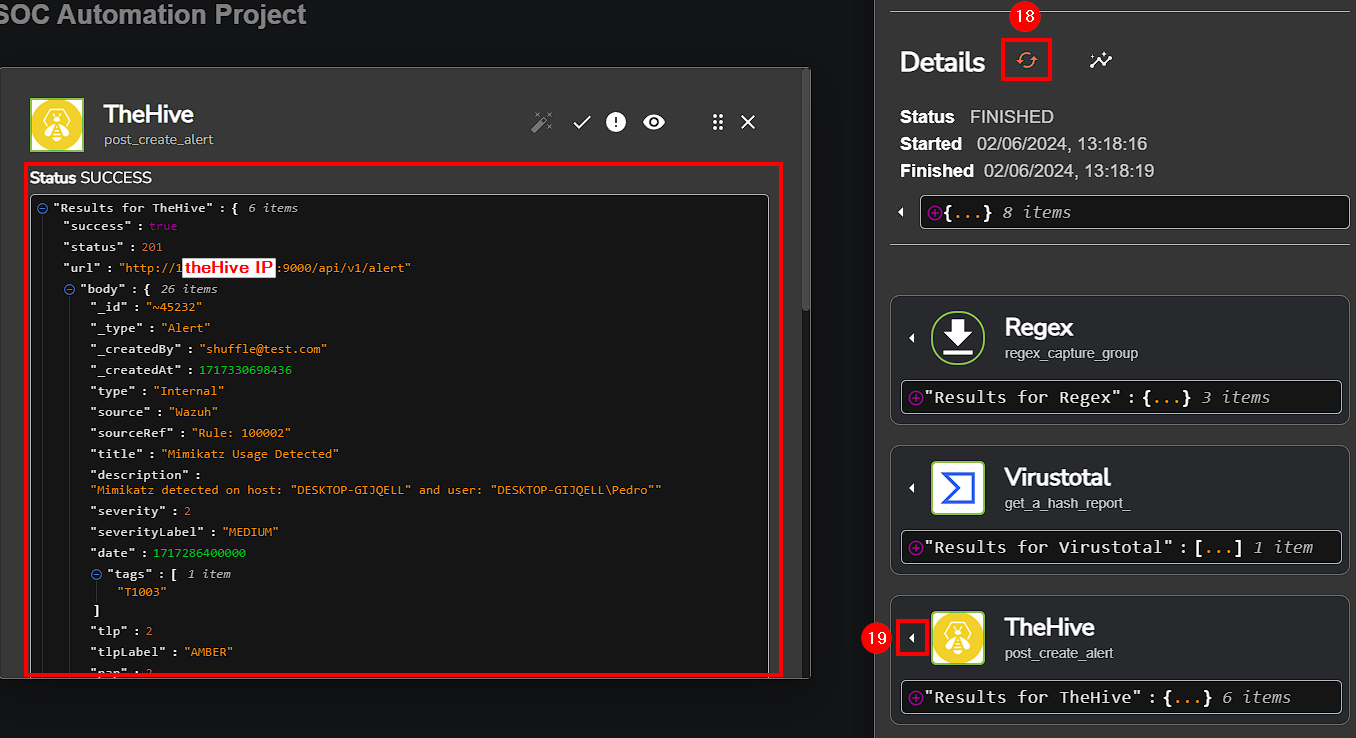
Save all modifications and rerun the workflow to see if it is working.
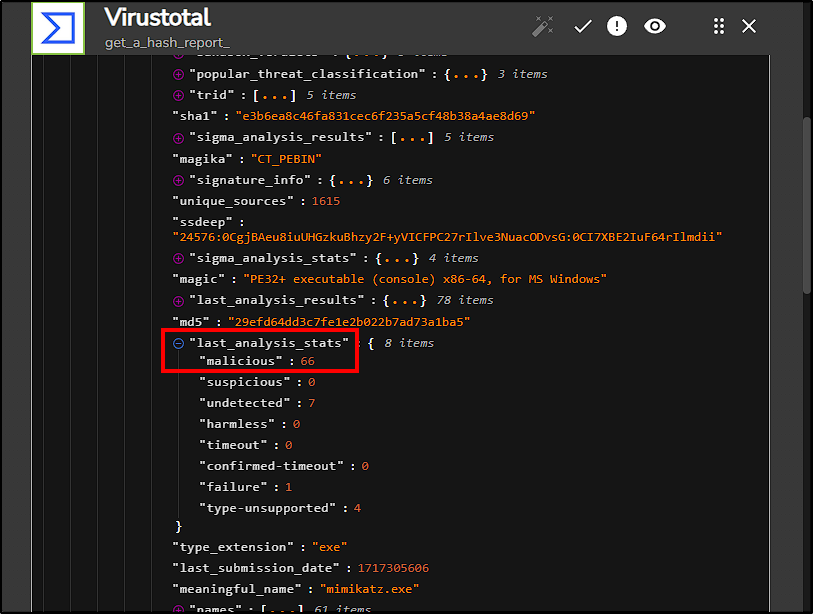
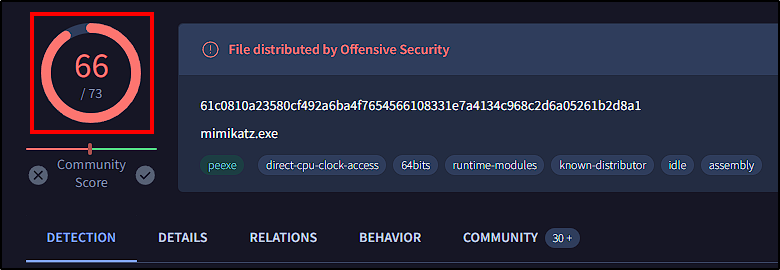
Upon execution, VirusTotal successfully got the file report, giving us detailed information about the file reputation.
TheHive Integration
Our next step, is to forward all these details to theHive to initiate alert creation for effective case management.
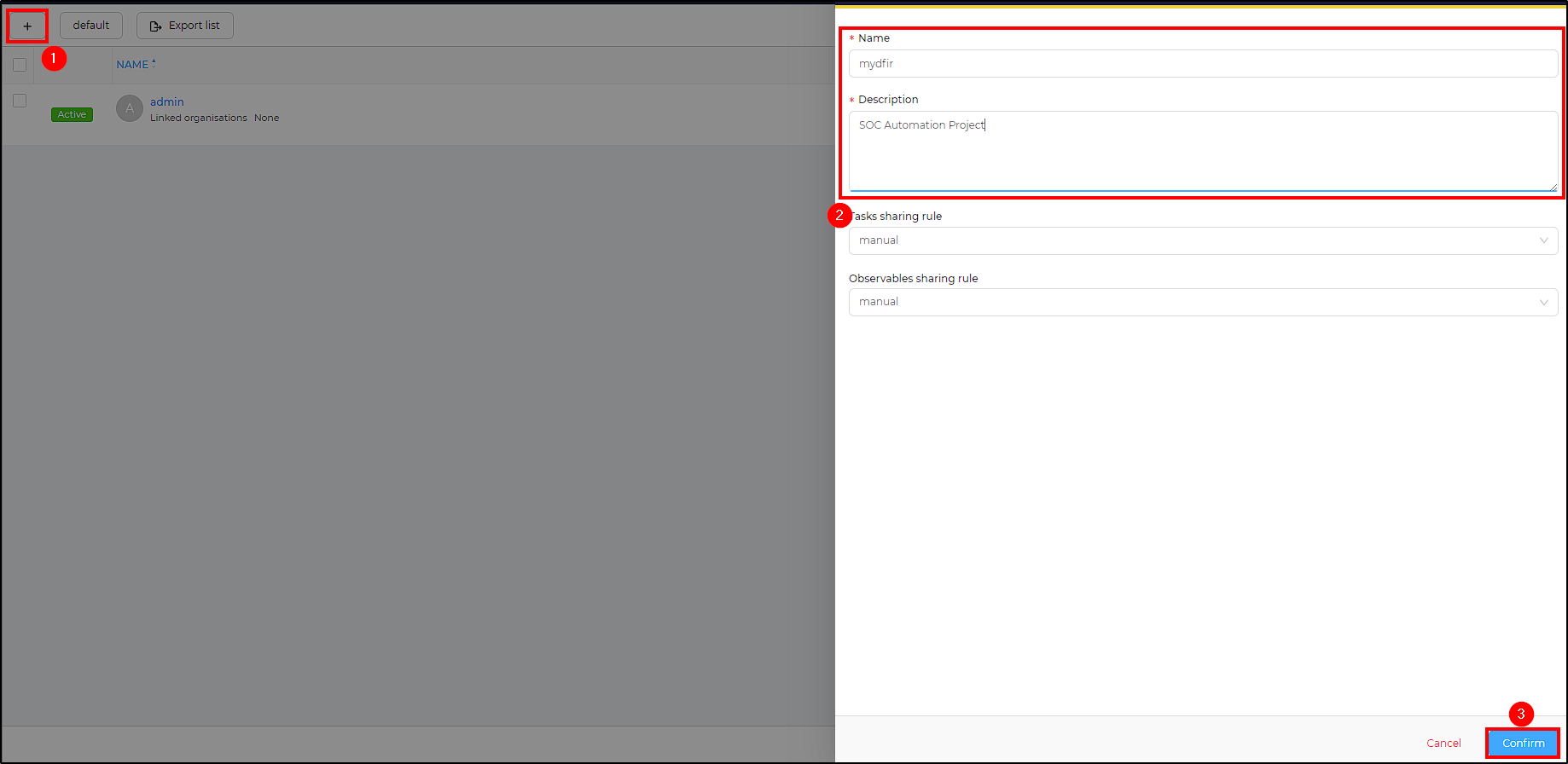
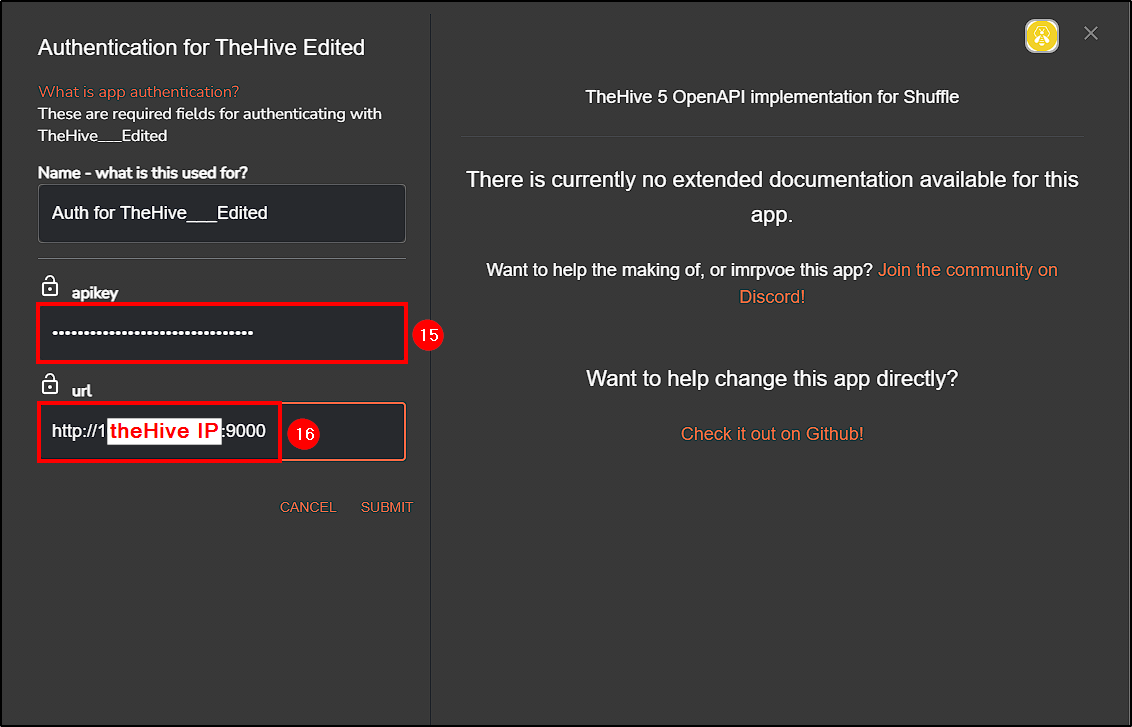
First, log into theHive web interface at https://"theHive_IP":9000 and create a new organization where Shuffle alerts and information will be received.
To do this, click on the + sign, name the new organization and proceed with its creation.
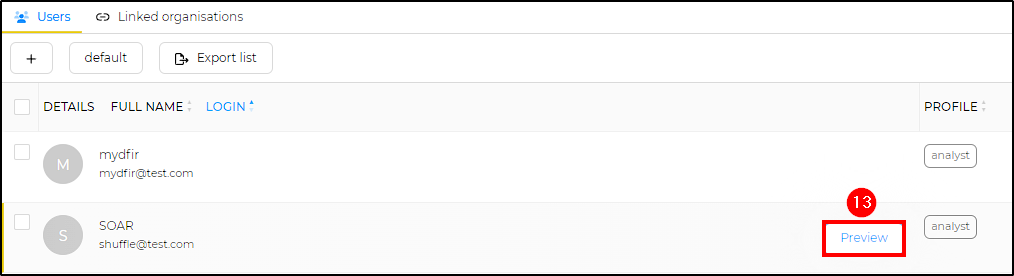
Following that, we will need to configure two users: one for accessing our organization to monitor alerts ([email protected]) and another as a service account to provide an API key for authentication on Shuffle ([email protected]).
Navigate to the new organization and select the + sign to add users.
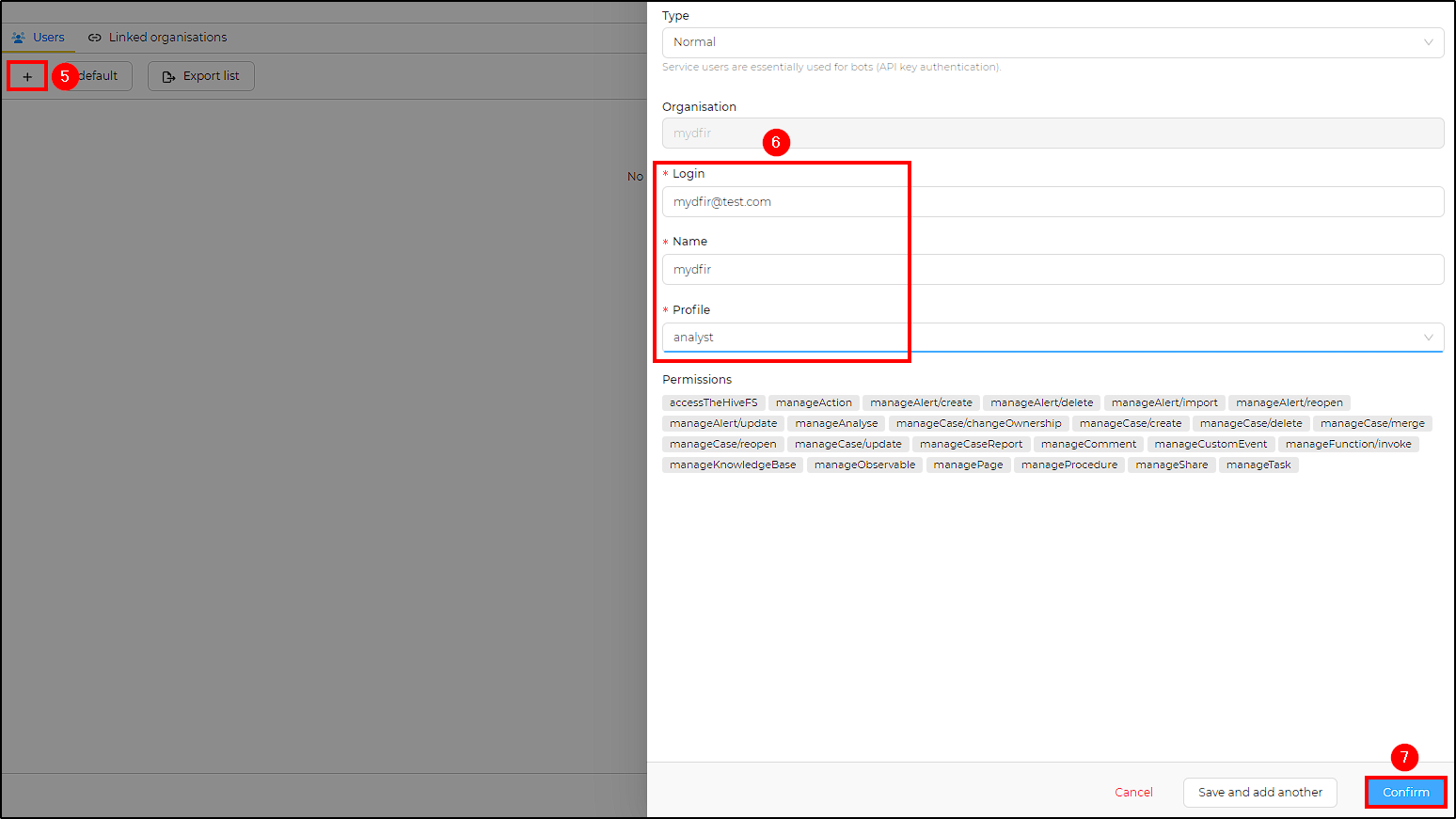
- Normal user:
- Login: [email protected]
- Name: mydfir
- Profile: analyst
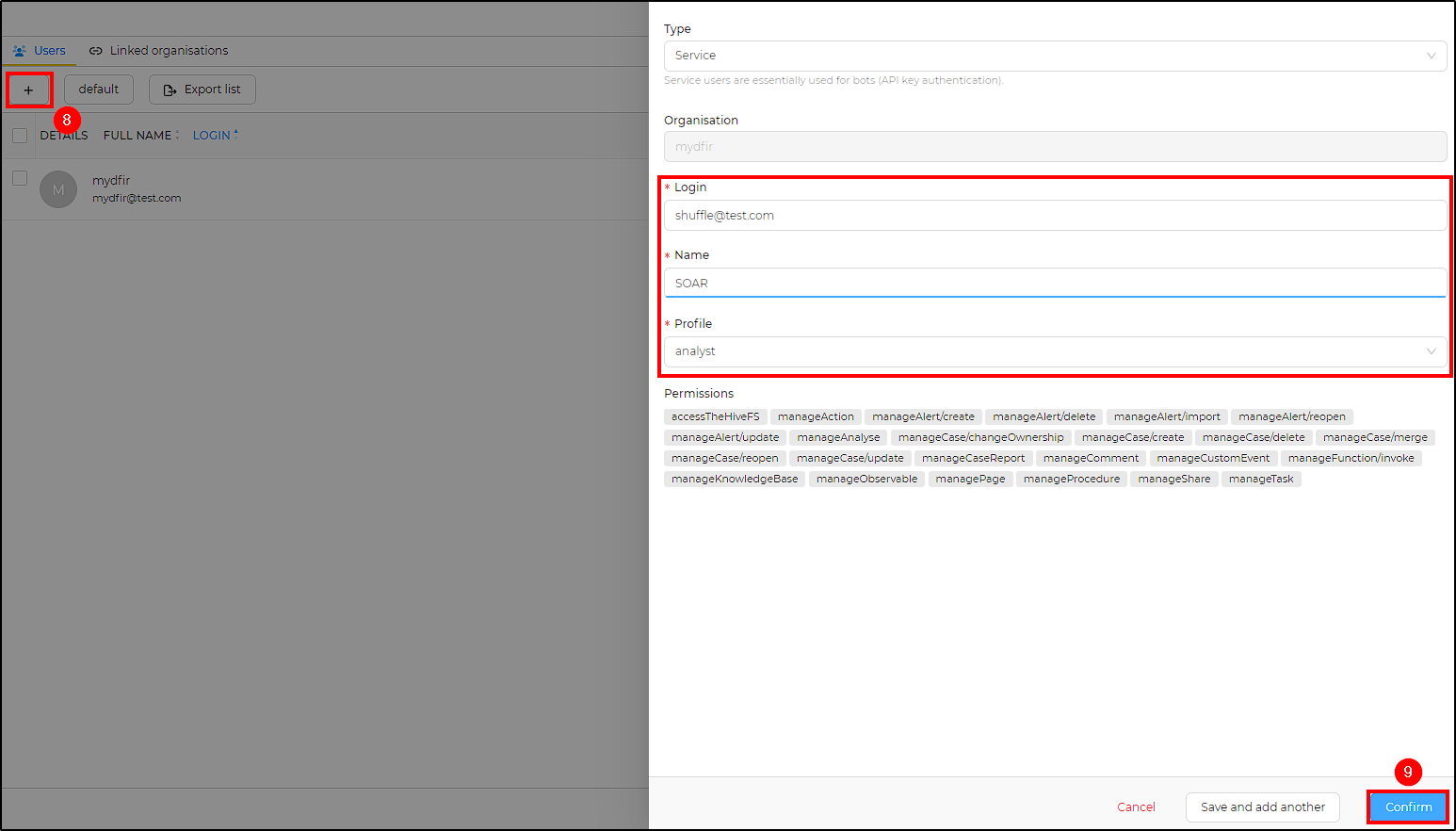
- Service account:
- Login: [email protected]
- Name: SOAR
- Profile: analyst
When assigning permissions to service accounts, it’s crucial to implement the Principle of Least Privilege (PoLP).
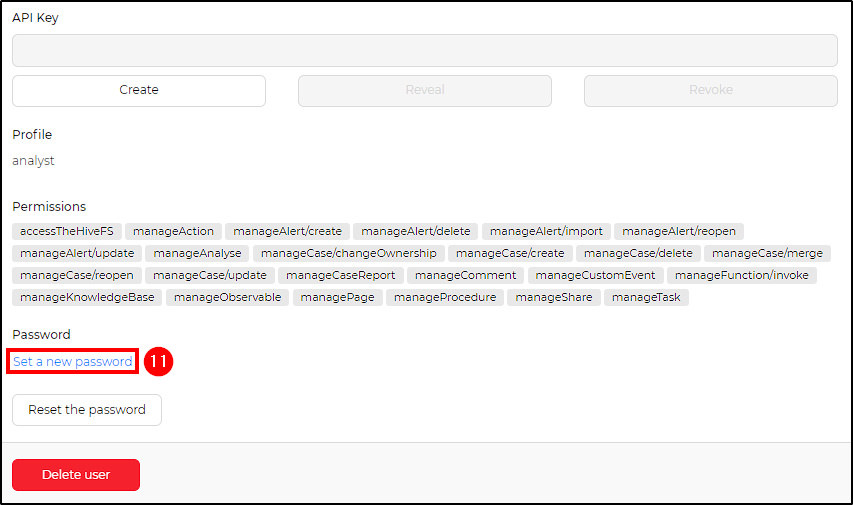
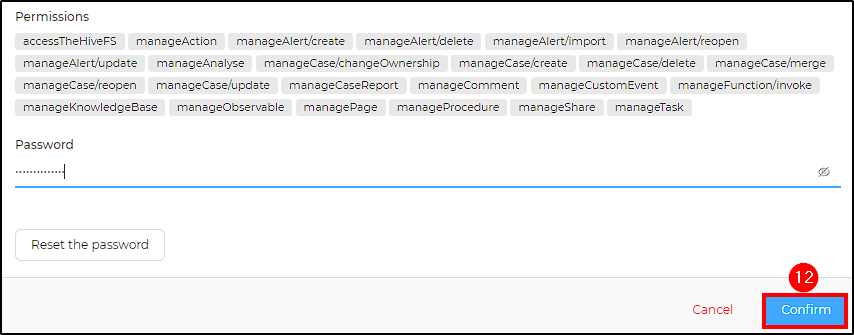
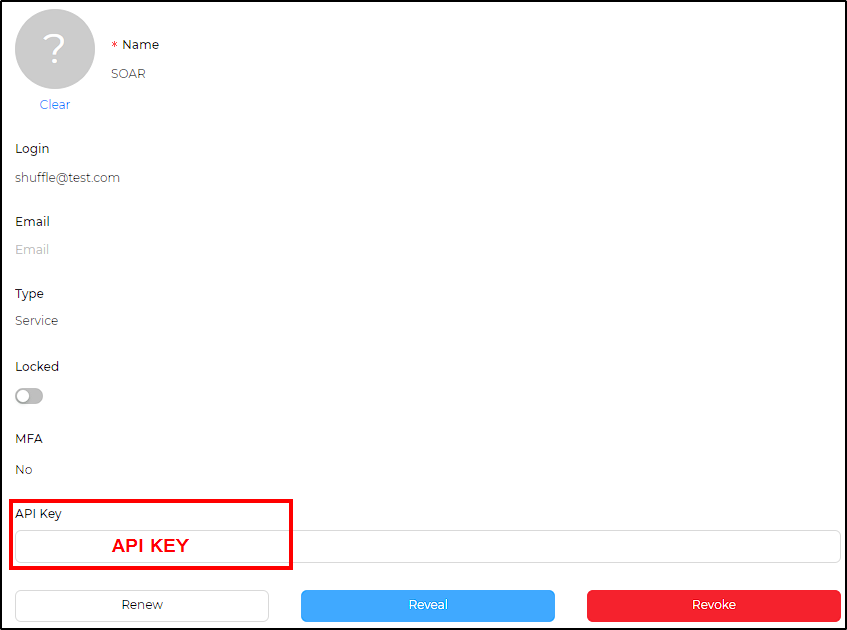
Complete the user configuration by setting a password for mydfir and generating an API key for shuffle.
To set a new password, go to Preview > Set a new password > Confirm.
To generate the API key, go to Preview > API Key > Create > Confirm.
Creating Alerts
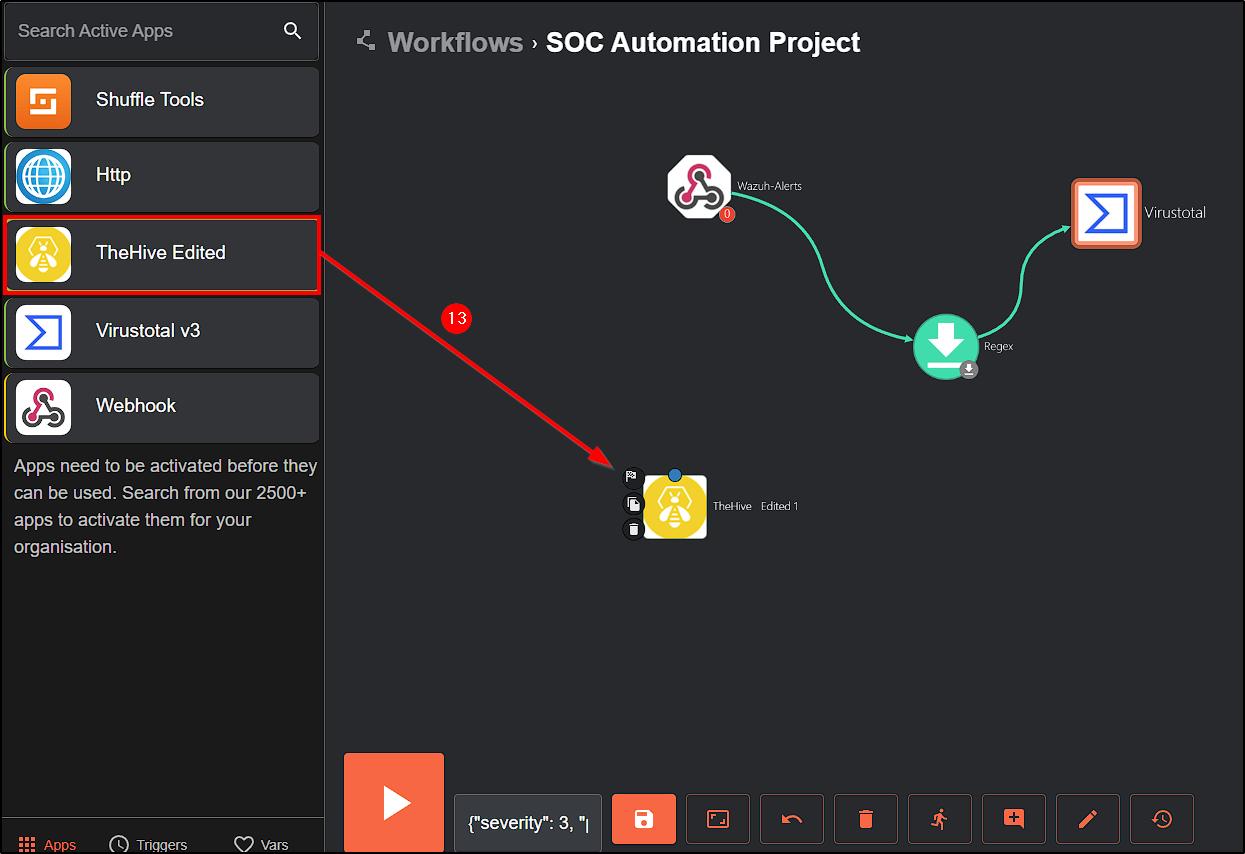
Now that the organization and users are set up, return to Shuffle and drag the theHive Edited app into the workflow instance.
Authenticate using the API key obtained from the shuffle user and configure the URL to theHive’s server IP.
Connect theHive to VirusTotal and configure the following parameters:
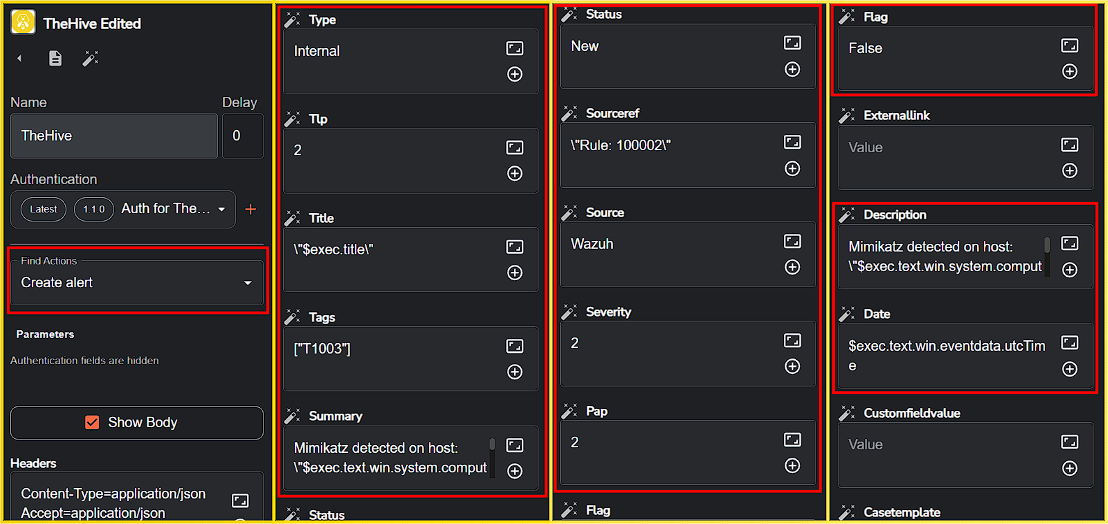
- Find action: Change it to
Create alert.
The next parameters are not required. The next values are from my configuration.
- Title: Change it to
$exec.titlevalue from Execution Argument. - Tags:
["T1003"] - Summary:
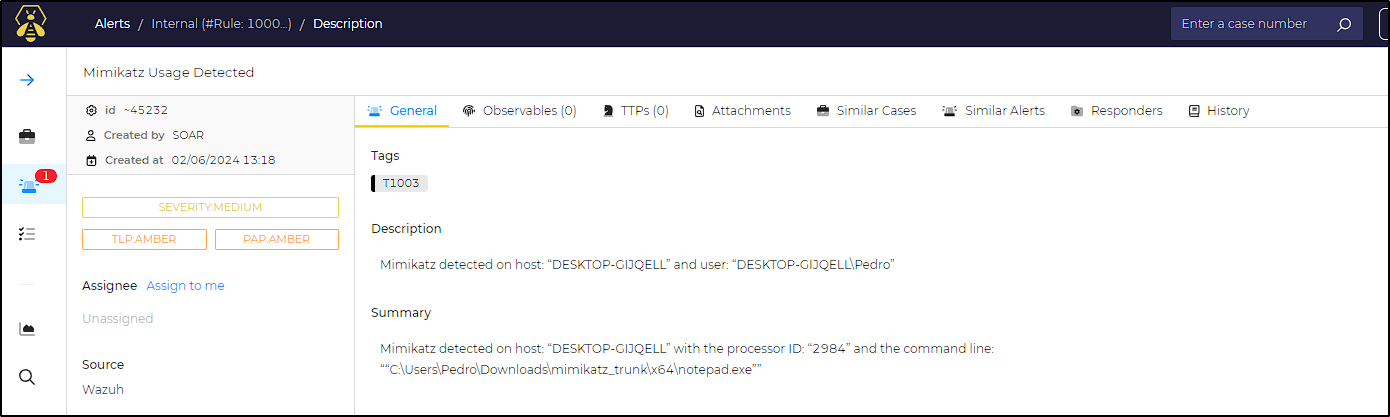
Mimikatz detected on host: $exec.text.win.system.computer with the processor ID: $exec.text.win.system.processID and the command line: $exec.text.win.eventdata.commandLine - Severity:
2 - Type:
internal - Tlp:
2 - Status:
New - Sourceref: Change it to the rule ID.
- Source:
Wazuh - Pap (Permissable Actions Protocol):
2 - Flag:
False - Description:
Mimikatz detected on host: $exec.text.win.system.computer and user: $exec.text.win.eventdata.user - Date: Change it to the
utctimevalue from Execution Argument.
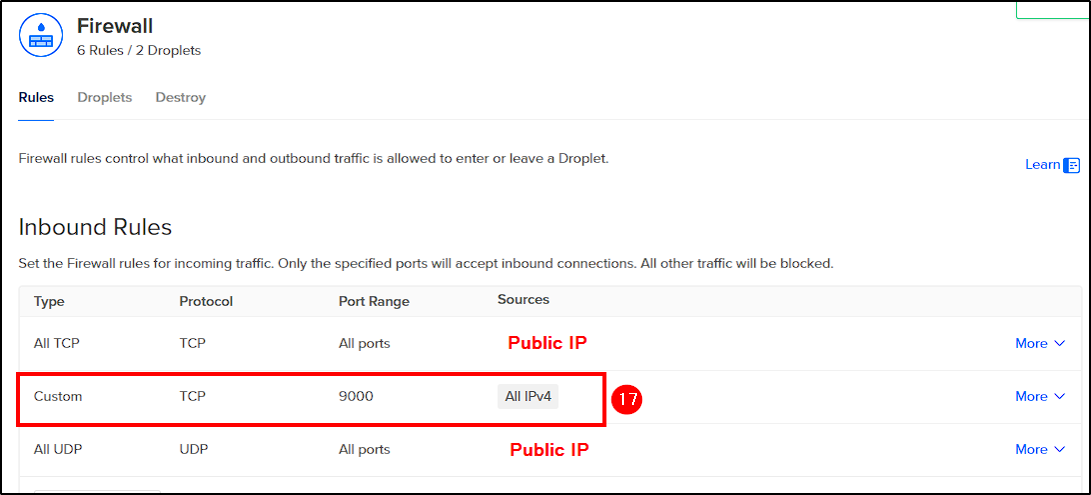
Save the changes and before testing the Workflow, create a firewall rule in DigitalOcean to allow traffic to port 9000. This will enable Shuffle communications with theHive server.
Finally, log into theHive web interface with mydfir credentials and rerun the Workflow.
After refreshing theHive dashboard, we are able to see the alert and its content.
Notifying Analyst via Email
Our final step involves setting up email notifications for every alert occurrence.
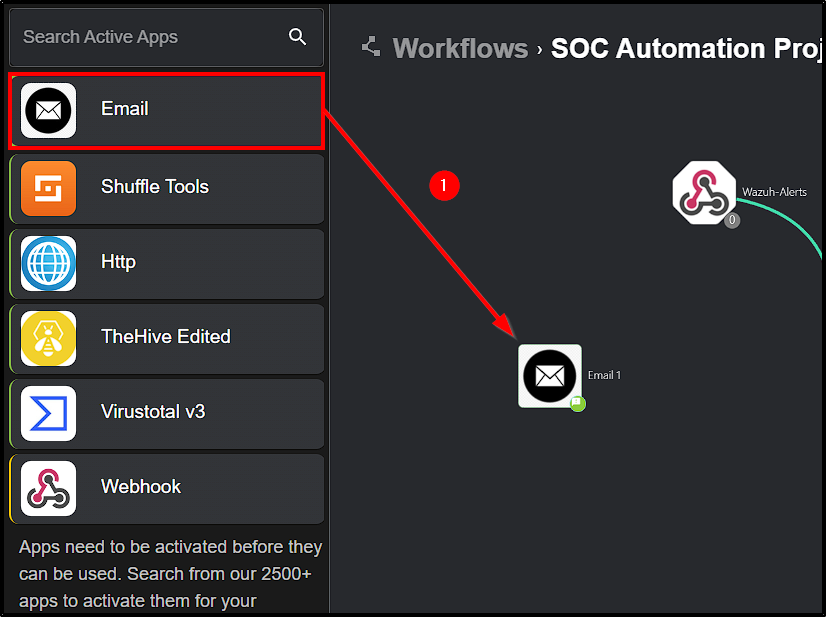
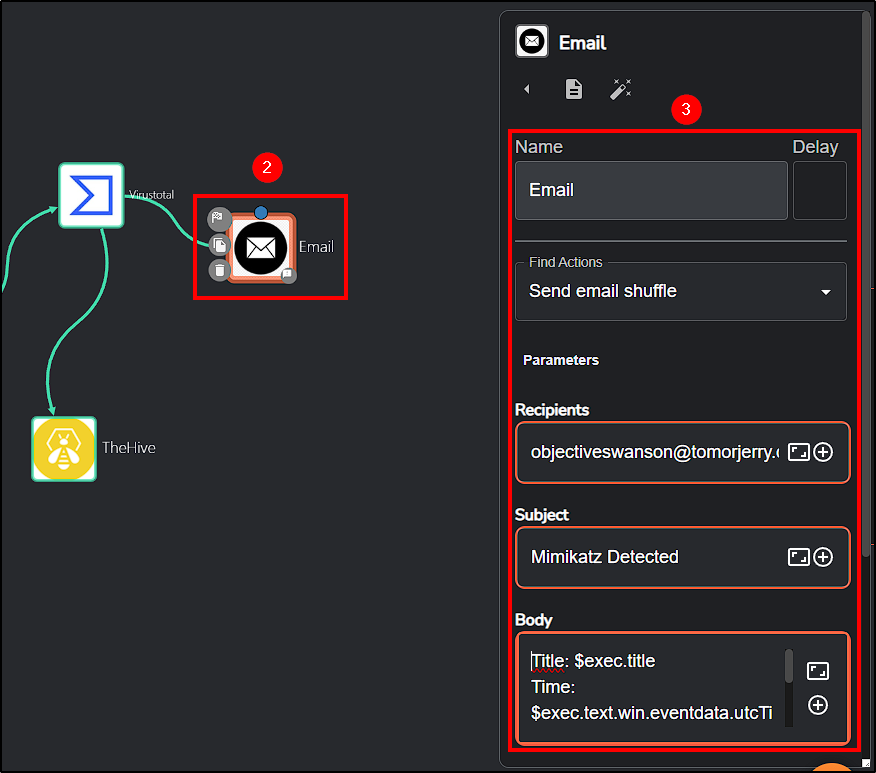
To implement this, add the Email app to the workflow instance in Shuffle and connect it with VirusTotal. Make the following adjustments:
- Recipients: Change it to your email address (we’ll use squarex disposable email feature)
- Change the Subject and Body to your liking.
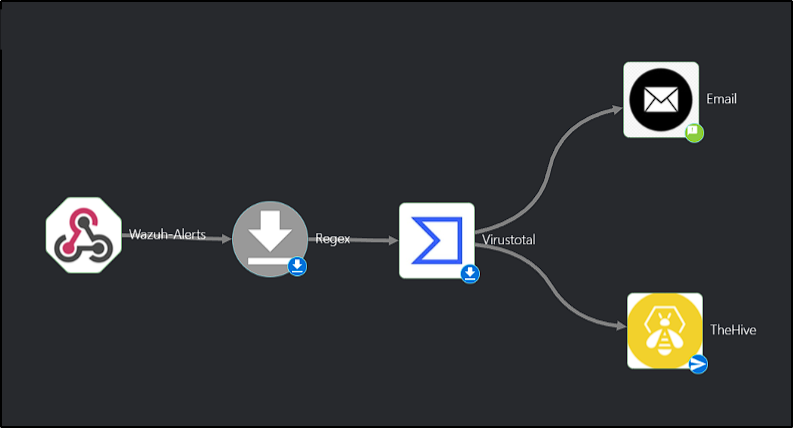
The final Workflow should look like this:
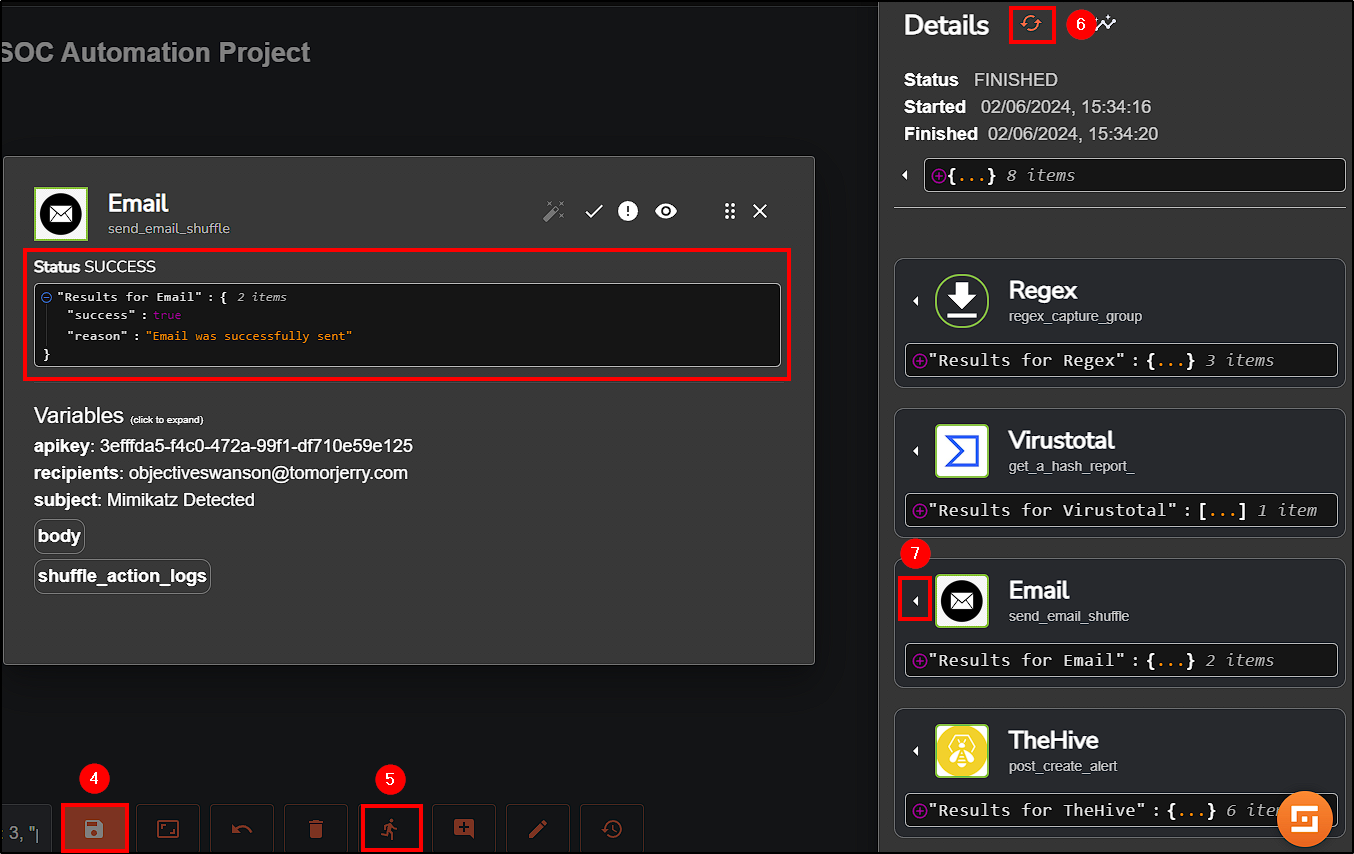
Save the changes and rerun the workflow again.
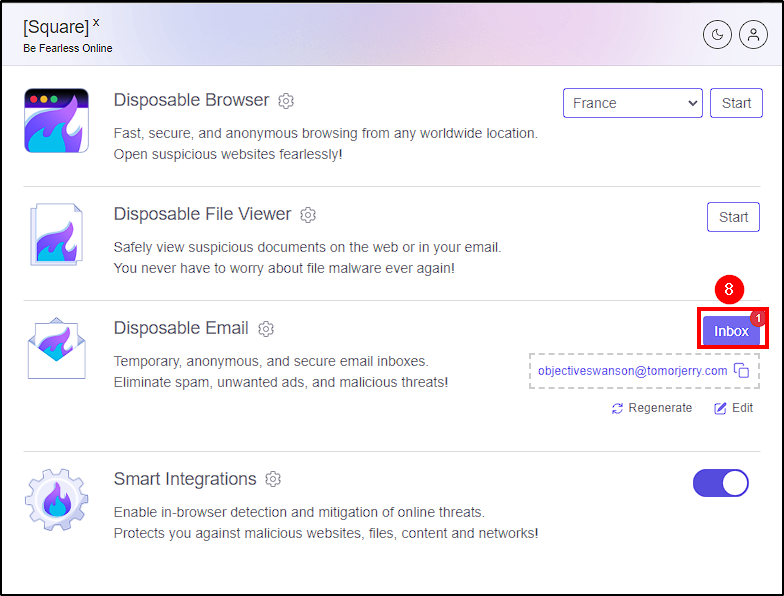
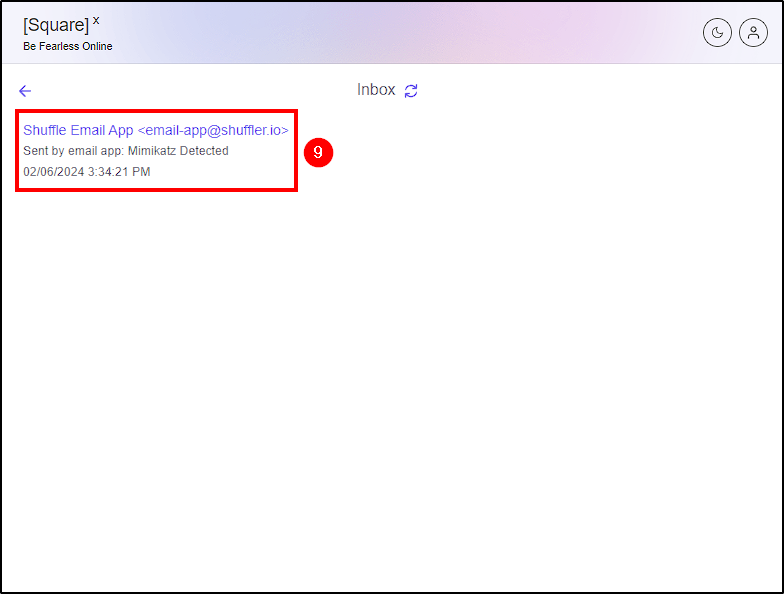
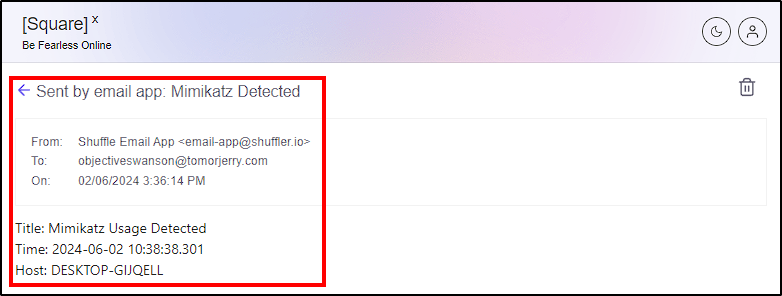
From Shuffle we can see that the email was sent. To confirm this, we can check squarex email inbox.
With this step, our project is now “complete”. While this setup was simple and straightforward, the potential to create more sophisticated playbooks using Shuffle, integrating with tools like Cortex or MISP, is immense.
Final Thoughts
This project has been a rewarding journey, demonstrating the power and flexibility of open-source tools. Integrating Wazuh, theHive, and Shuffle has given me valuable hands-on experience and a deeper understanding that will be beneficial in future projects. Despite its simplicity, configuring, troubleshooting, and researching documentation throughout this lab setup have equipped me with essential skills that will be fundamental in my career.